Scientists HACKED A Human By Controlling A Person With Another Person's Brain (Video)
Aug 28, 2013 19:56
Here's a scary piece of science: Researchers at the University of Washington have figured out how to send commands from one person's brain to control a different person's muscle movement. Are we at the era of HUMAN HACKING?
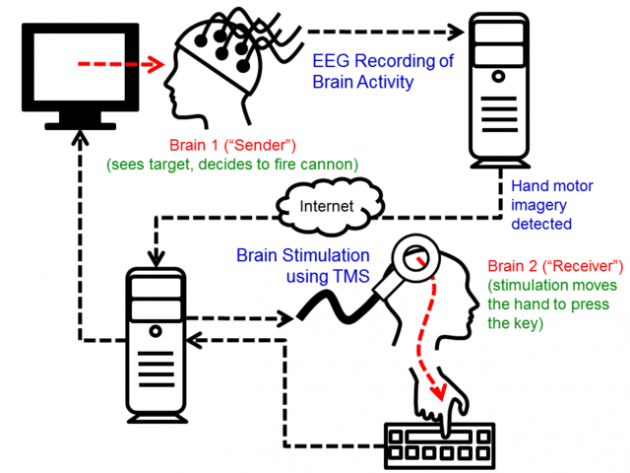
Computational neuroscientist Rajesh Rao sat wearing an electroencephalography cap. Dr Rao watched a simple computer game, firing a cannon at a target, and that moment, he imagined moving his right hand to hit the fire button. He did not actually move his hand,
Across the campus, his colleague, Professor Andrea Stocco, wore a cap holding a transcranial magnetic stimulation coil. It stimulates muscle control regions of the brain with a magnetic impulse and wore noise blocking earplugs and faced away from the video screen.
The signals sent from Dr. Rao's cap to Dr. Stocco's cap triggered Dr. Stocco's finger hitting the "fire" button on Dr. Rao's command.
This is so Ghost in the Shell concept. And it's surreal that its already happening. The tools used were the electroencephalogram cap that picked up the brain activity, and the transcranial coil that transmitted it, and they've been used in scientific experiments for years.
The University of Washington team claims this is the first human-to-human brain interface.
Dr. Rao points out that this only reads muscle signals, and not thoughts, and it can't make you move against your own will.
“I think some people will be unnerved by this because they will overestimate the technology. There’s no possible way the technology that we have could be used on a person unknowingly or without their willing participation.”
But either way, this is really just the beginning. The applications are endless, not to mention, some may be malicious too in the future. It could someday be used by a pilot on the ground to help land an aircraft. Or it could help immobile patients to express themselves physically. Human hacking. Scary.
[University of Washington]