Why there needs Asymmetric Encryption in Public Key Infrastructure?
Aug 26, 2021 19:43
Information security has proved to be a colossal factor, especially with modern communication networks. That said, there are chances of leaving loopholes that could increase to the level to foster devastating effects. Public Key Infrastructure (PKI), aka PKI, certificate automation serves as digital certificates used to validate and identify the connection between server and client.
It has a close relation to the connections formed that is very secure and trusted. Discussion on popular encryption schemes to tighten communication security in Symmetric and Asymmetric Encryption is a must. PKI governs encryption keys, and it does so by issuing and managing digital certificates. Digital certificates, also called X.509 certificates and PKI certificates, serve as the electronic equivalent of a driver’s license or passport.
Need for Asymmetric Key Cryptography
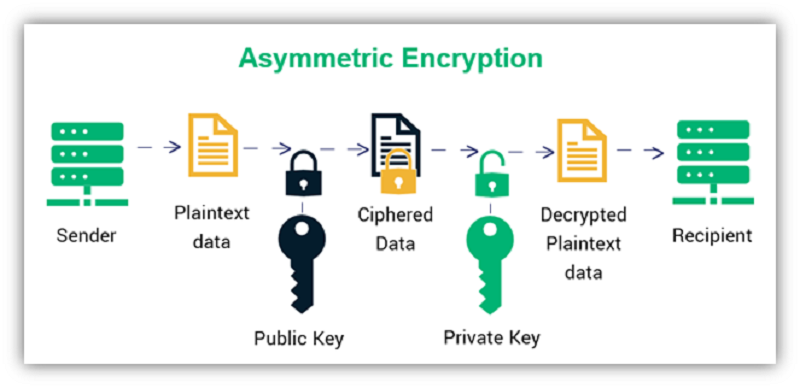
Asymmetric encryption proves to be one of the best platforms for securely exchanging information without the requirement of sharing private keys. It utilizes a public key pairing that involves the method of getting data encrypted with the private key. It can only be decrypted with the public key. TLS (or SSL) protocol makes HTTPS possible and completely relies on asymmetric encryption. Asymmetric encryption verifies third parties that you’ve not got the opportunity to meet via public channels that are insecure.
Moreover, the asymmetric encryption keys are large asymmetric public and private keys in the form of long strings of random numbers. It involves separate keys, leading to the slowed-down process considerably. However, it is best for securing data & key exchanges in public channels. Public key infrastructure (PKI) works in the form of a framework of policies, processes, and technologies that make secure third-party communications possible.
Asymmetric and symmetric encryption is equally important. Symmetric Encryption proves to be a lot quicker compared to the Asymmetric method but, remember that the security is enhanced with Asymmetric Encryption. Learn more about how does asymmetric encryption work in detail. Certificates created individually depending on the scale of operations also serve as SSL/TLS certificates.
This Asymmetric encryption method also overcomes the lacuna of Symmetric encryption, and it does so by exchanging the key alone with the help of the public key/private key in an asymmetric way. It does so while still exchanging high-volume data using symmetric mode. Website owners secure the communication between a website (server) and the client (browser) with the help of these PKI certificate automation methods. Both Asymmetric encryption and symmetric encryption have got their individualized benefits and drawbacks. Sometimes, there is also a need for both protocols. Based on the needs, it's good to decide on the choice.
Different applications of Asymmetric Encryption
1) Confidentiality
The most common application of Asymmetric Encryption is the maintenance of confidentiality. Sending critical information by encrypting it is the method here. In the process, it incorporates the receiver’s public key and decrypts it with its private key.
2) Authenticity using Digital Signatures
The sender attaches a private key to the message in the form of a digital signature and exchanges it with the receiver. In this process, there is the involvement of the method of the receiver using the sender’s public key and verifying whether the private key sent belongs to the sender. That said, it helps in ascertaining the sender’s authenticity.
3) Integrity developed with the help of the Information Exchange
The Hash of the data gets exchanged, creating and encrypting using the sender’s private key. Encrypted hash and data find an exchange with the receiver. The sender’s public key helps the receiver decrypt the hash and recreates the hash. The difference between the two hashes indicates the content gets altered after there is a loss of signature and integrity. The integrity check is the method that is involved in digital cash and Bitcoin transactions.
4) Non-repudiation
Digital signature encryption tool is proving to be the best where the owner of a document or information exchanging with others cannot disown the content.
Final Words
Public key infrastructure ensures offering information about an individual or entity. Both Symmetric and Asymmetric encryption finds use in different places. Symmetric encryption is easier, but Asymmetric encryption is the safer one. No one can give a guarantee regarding one being better than the other. In different ways, Symmetric and Asymmetric encryption are also very productive and, depending on the mission, one or both finds use individually or together.